Computer Security Day was launched after the first computer virus attacked Cornell University in 1988 and has been an annual event to raise awareness ever since. Things have moved on since 1988, but the threat from cybercrime is more serious than ever.
Cybersecurity is much more than securing our laptops and desktop computers. Think of all you do from your smartphone or other mobile devices. How many purchases have you made with a credit card? How many friends do you wish a happy birthday? How much personal information do you share with friends and businesses without even realising it?
For businesses, hacking has evolved and ransomware has now become a constant and primary threat. Hackers hold information “hostage” until the company pays to get its access back.
So how can you, as a business or personal user, do more to protect your online data?
Our recommendation is to move beyond passwords. Arguably, there's no better protection.
It's widely believed that it's not enough to simply use a strong password anymore, as the tools to hack have become more comprehensive, from keylogging to advanced social engineering. Websites such as https://haveibeenpwned.com/ offer a free service to check whether your email has appeared in a global database of hacking leaks. If you find your address there, we strongly recommend that you change all of your passwords.
One way to move beyond passwords is to use passwordless or 2-Factor authentication
2-Factor authentication is essentially an extra layer of security, which is required in addition to your password. This is typically a randomly generated number (one-time password) that only your device and the website you are trying to login to, understand. One-time passwords can be generated both on physical keys or by using software on your phone (Google Authenticator, Microsoft Authenticator).
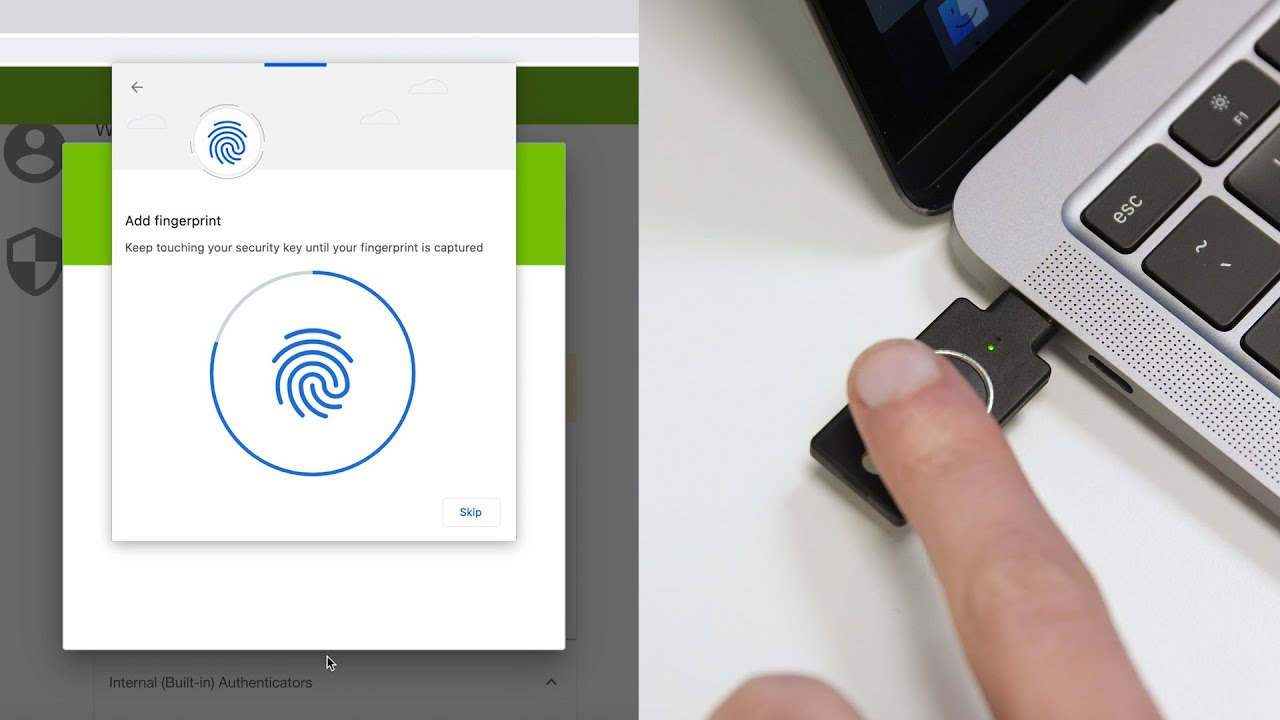
This extra layer of security reduces the likelihood you will be a victim of cybercrime, although this is still no guarantee of safety, so always remain vigilant when logging in to any website or application.
2-Factor technology is evolving fast, our partners Yubico are now offering their first generation of biometric keys. That means the additional layer of security can be tied to your fingerprint using a small USB device that can be plugged into any USB port. This also opens the door for passwordless logins, which do not require you to type anything in, but simply confirm your biometric data, either with your fingerprint or using facial recognition. Yubikeys also work with mobile phones, so we can share the same security devices between our laptops, desktops and phones.
We’ve witnessed the mass adoption of facial recognition login with our mobile phones, which has now largely replaced the pin as the default login process, so a move away from one-time passwords to a more robust, biometric lock is the logical next step in securing our data.
These extra layers of security do require website and application developers to integrate and upgrade their login services and we have seen more and more providers start to adopt these protocols, but there is still a long way to go before the majority are adhering to the latest security standards.
Use different passwords with every application in a sustainable way
Another recommendation is to use different passwords for every website and to store those passwords inside a password vault, such as LastPass.
LastPass can be installed on your computers and mobiles, giving you access to the passwords wherever you are. It automatically fills in the password when needed, so there’s no need to remember them all. By reusing the same password between websites you are exponentially increasing your risk, as one compromised platform can reveal data that could be used to login to many other sites where you have shared the same password.
We've designed AuthStack to secure our customers and their end users
To help businesses secure their users and data, we've developed Authstack, a host-anywhere, enterprise-grade single sign-on (SSO) and identity access (IAM) system. It’s a simple and intuitive way to centralise user identity management so users only create and maintain one password and one 2-factor security device to login to multiple applications which are all connected.
Designed for security-conscious enterprises, AuthStack integrates with thousands of apps, uses existing user databases and supports 2-factor authentication.
Think of it as the padlock between our clients’ apps and their customers and third-pay apps.
AuthStack also generates a variety of reports, so clients can further explore how their apps are being used and kept secure.
AuthStack is garnering acclaim for its innovative security, reliability and open-source security frameworks.
For more information or to request a 30-day free trial of AuthStack visit: https://www.authstack.net
Tags:
security authstack cybersecurity cybercrime passwordlessPublished by: Iva Pervan
Published on: 30.11.2021



 Facebook
Facebook Instagram
Instagram LinkedIn
LinkedIn Twitter / X
Twitter / X