This article assumes that vulnerable operating systems, such as Windows XP, cannot be upgraded in the short term, and therefore, what options are available to help mitigate the risk.
Most of us have now heard about WannaCrypt (also known as WannaCry) ransomware and the damage it caused to the NHS and other companies and institutions around the world. If you haven’t heard about recent events you can read more over at Microsoft: https://blogs.technet.microsoft.com/mmpc/2017/05/12/wannacrypt-ransomware-worm-targets-out-of-date-systems/
Note: Microsoft have released a patch for WannaCrypt/WannaCry for all affected Windows versions, including unusually, Windows XP (since it’s past official support): https://blogs.technet.microsoft.com/msrc/2017/05/12/customer-guidance-for-wannacrypt-attacks/
WannaCrypt ransomware is being delivered by the recently leaked NSA hacking tool (Double Pulsar). There was a quieter period after the “killswitch” was activated (a set of hardcoded domain names, which if registered and resolvable, would stop the application spreading).

But, new WannaCrypt iterations are being created, mitigating this “fix”.
Sadly, there are still countless IT systems running on vulnerable unsupported operating systems, such as Windows XP or older, which are easy targets for hackers since the software vendors, such as Microsoft, have stopped providing security updates. Upgrading the OS is often not a simple process, especially if the software running on the OS doesn't support the newer version. This makes upgrades costly and expensive, since the legacy software must also be upgraded, and what happens if the original vendor has gone out of business, or the upgrade is cost prohibitive? There are many potential complications and challenges which explain why many companies continue to use legacy software on vulnerable operating systems.
When engaging with our customers and the professional community at large, we hear from CTOs and IT managers struggling with technical debt. They tell us upgrading is not a top priority, because “it just works”, or “we’re awaiting a new system which should be ready in X months”. Other times it’s a lack of internal resources or just a lack of CIS (Continuous improvement strategy) within the company.
Whatever the reasons, if you are reading this article and operate vulnerable systems, you are probably researching what options you may have. We have detailed a few of our ideas below.
Option 1: Virtualise the vulnerable operating system
Ransomware viruses, such as WannaCrypt, encrypt all your files and do not present an easy recovery option. There is usually no way to boot the operating system into any sort of recovery mode and roll back to an earlier state; not that system restore or related tools would help you much, since your files are being encrypted and are unrecoverable without the decryption key, making traditional recovery a futile option.
To summarise the steps; the first requirement is to create a virtual machine image from the original vulnerable system. Then, using the original (or new) hardware, install a newer, supported operating system, then run the older operating system as a virtual machine sat on top (this newly installed operating system is known as a host, the old operating system, now virtualised, is known as a guest).
This setup enables the possibility of snapshotting the vulnerable operating system (which is now a virtual machine), and all its files, regularly, and at the click of a button. If any issues occur, you can roll back to a previous state as required.
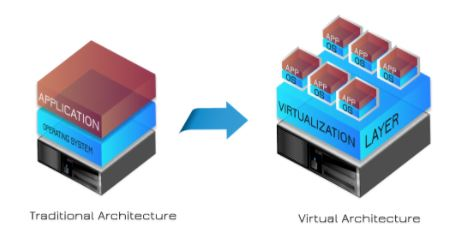
As most older operating systems are 32 bit, they will not require advanced virtualisation features from your processor, such as VT (Intel Virtualisation Technology). This is especially useful if you need to continue running the older hardware. Without VT, the system will run slower, but the tradeoff is worth it in this case.
Virtualisation also provides the opportunity to upgrade the computer hardware without fear of backward compatibility, since the older hardware can be emulated - this may also be a consideration as older hardware tends to become less reliable (especially hard disks).
There are various virtualisation options on the market, some paid and others free.
- We are fans of open source and the security and stability offered by using Linux, so our first recommendation is to install Ubuntu 16.04 as a host machine, combined with a virtualisation stack on top.
- On the lower end of complexity is VirtualBox, which offers point and click virtualisation. With this software you can get setup very quickly.
- Here is a guide on how to migrate a physical Windows XP machine to a VirtualBox image. Forewarning: Windows XP isn’t the easiest OS to migrate. This is due to the way Windows XP sets up and configures its HAL and IDE drivers, but it’s achievable by following how-to guides.
- https://www.virtualbox.org/wiki/Migrate_Windows
- On the lower end of complexity is VirtualBox, which offers point and click virtualisation. With this software you can get setup very quickly.
- Hyper-V on a later Windows platform (such as Windows 10)
- Migrate your old OS to a virtual machine image with the Microsoft Tool (Disk2vhd)
- This tool creates a virtual machine image from a running physical machine, which can then be booted within Microsoft Virtual PC or Hyper-V. If this option is preferred, then it is recommended the new host operating system is the latest Windows 10, with Windows XP or 7 running as a guest virtual machine
- VMware vSphere
- Build a dedicated VMware server (or more, depending on your requirements)
- Migrate your legacy Windows machine to a VMware image
- Access the old Windows (now a virtual machine) using remote desktop services from a new computer, running a supported OS.
Once your chosen virtualisation platform has been set up and the virtual machine is running, the next step is to enable daily snapshotting of your virtual machine, with at least 7 days of full backups.
Note: This can use a lot of disk space, but you may have to rollback a few days to find a clean restore.
Useful links
- This process details how to manually snapshot in VirtualBox
- Automating the snapshots is a better solution, this article references a bash script which will trigger a VirtualBox snapshot via cron
- The following articles detail how to take snapshots in Hyper-V and how to rotate older snapshots
- Vmware vSphere snapshotting
Summary
While this is not a simple solution, It abstracts the vulnerable operating system and provides you with more control if the machine becomes infected. It also allows for network isolation which may not have previously been an option.
Option 2: Try and decrypt the files
If you are faced with an already infected computer, without adequate backups and/or need to get operational fast, you can try to decrypt the files. Over the last few days, various tools have been released which can scan the memory of the computer and locate prime numbers, then reverse engineer the encryption key, making it possible to decrypt your files under certain circumstances. This option is very smart, but not without pitfalls. Decryption is possible as long as the machine has not been rebooted since it was infected and if you haven’t waited too long (the memory space where the prime numbers are stored can be overwritten).
So far it has been reported to work on XP and 7, but various iterations of Windows of the same generation are also supported (Windows 2003/2007/2010), etc.
In the case of WannaCrypt, decrypting files is possible with WanaKiwi.
https://github.com/gentilkiwi/wanakiwi
Decryption in action

Wanakiwi also recreates the .dky files which the ransomware expects upon successful payment, preventing WannaCrypt from encrypting more files.
Option 3: Perform regular, incremental backups of all your files
This option may sound obvious, but mounting a network drive from an infected machine presents obvious challenges. The files on the mapped drive will likely be encrypted too once WannaCrypt starts.
However, it’s possible to set up backups in such a way that the backup system connects to your computer and synchronise the files, rather than your computer connecting and mounting remote drives.
Open source software offers cost effective options for this. We have been using BackupPC for a number of years. Despite its name we use it to backup server(s) securely, it offers deduplication, incremental backup and other advanced backup functionality. Backups are performed using rsync, which is available on Windows with a client installation. http://www.michaelstowe.com/backuppc/
This is most effective when combined with Option 1, which will provide both full snapshot and easy rollback options with incremental backups throughout the day.
Option 4: Isolate the vulnerable machines from the Internet and shared networks
One option is to effectively quarantine the vulnerable machines into their own virtual LAN without Internet access. Setting up groups of vulnerable machines into different VLANS can help slow down the infection.
Machines which are totally isolated probably require a manual process for moving files around , which can be achieved with USB keys, or by dropping files into a quarantined storage (see option 3). But, using USB has its own drawbacks, with some Crypto ransomware viruses having morphed the ability to use USB as a proxy to your vulnerable machine.
To summarise
With the options above, it is possible to provide some level of “damage limitation” caused by malware and ransomware, but it’s clear that prevention is better than cure. Every company which runs and relies on software should have a clear and defined continuous improvement strategy (CIS) being devised or set in motion. A modern CIS programme is key to ensuring your company remains ready to do business in a compliant and sustainable way.
If you would like more information about how to virtualise your existing legacy infrastructure and encapsulate it into modern hardware, or for a more general discussion about CIS strategies, contact us today. Our expert Managed Services team are on hand to discuss your challenges.
Thanks for reading,

Stuart Buckell



 Facebook
Facebook Instagram
Instagram LinkedIn
LinkedIn Twitter / X
Twitter / X